Private and public key pairs for SSH
To help validate identities, SSH has a key management capacity and related agents. When configured with public key authentication, your key proves your identity to remote SSH hosts.
An SSH-based identity consists of two parts:a public key and a private key:
- The private SSH key is the user's identity for outbound SSH connections and should be kept confidential. When a user initiates an SSH session to a remote host or server, he or she is said to be the SSH client. Through a mathematical algorithm, a private key is like your electronic identification card
- The public key is like the lock or gate mechanism that you present your ID card to. Your private key says, “This really is John Doe”; the public key says, “Yes, you are indeed the real John Doe; you are now authenticated: Please enter.”
Your public key represents who you will allow inbound access to through your gate or lock. Public keys need not be kept secret; they cannot be used to compromise a system or for unwarranted access into a system. On a UNIX or Linux system, these private and public key pairs are stored in ASCII text files; on Windows systems, some programs store the key pairs as text files, some in the Windows registry.
Multiple identifications using multiple private keys can be created with an SSH Protocol 2 configuration. Let's look at how to generate, set up, and configure an SSH private and public key pair on typical Linux hosts.
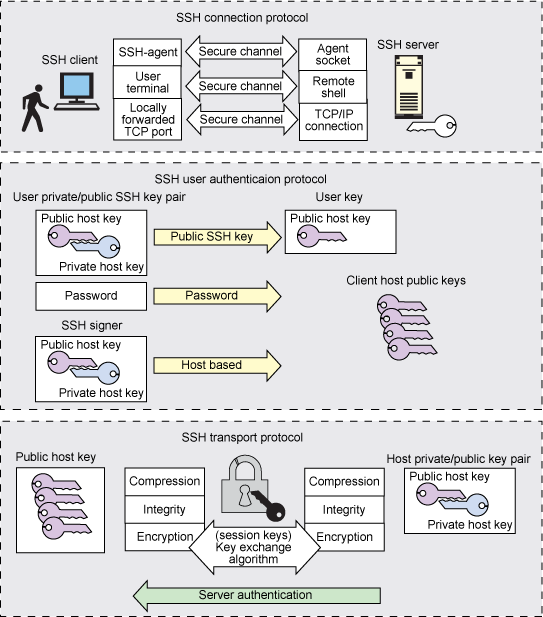
Configuring public and private SSH key pairs
The example shown below uses the ssh-keygen utility to create the SSH private-public key pair with the type of dsa.
mchurchi@church1e$ ssh-keygen -t dsa Generating public/private dsa key pair. Enter file in which to save the key (/home/mchurchi/.ssh/id_dsa): Enter passphrase (empty for no passphrase): ∗∗∗∗∗∗ Enter same passphrase again: ∗∗∗∗∗∗ Your identification has been saved in /home/mchurchi/.ssh/id_dsa. Your public key has been saved in /home/mchurchi/.ssh/id_dsa.pub. The key fingerprint is: 33:af:35:cd:58:9c:11:91:0f:4a:0c:3a:d8:1f:0e:e6 mchurchi@church1e
The following illustrates copying the public key of the key pair from the source to the destination host's authorized_keys file within the .ssh subdirectory under the home directory of the desired user account on the destination host.
mchurchi@church1e$ scp ‑p /home/mchurchi/.ssh/id_dsa.pub mchurchi@schlumpf:/home/mchurchi/.ssh/authorized_keys mchurchi@schlumpf's password: id_dsa.pub 100% 624 0.6KB/s 00:00
The following example, shows the first-time SSH command to the remote server thereby caching the key within your server's .ssh/known_hosts file. You enter the same passphrase with which you created the SSH private-public key pair, and the output of the command run on the remote destination server is seen locally back on your source server.
mchurchi@church1e$ ssh mchurchi@smurf ls /tmp The authenticity of host 'smurf (10.1.1.10)' can't be established. RSA key fingerprint is 48:f4:5e:00:b0:d7:45:0d:b1:e3:b2:69:20:43:14:52. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'smurf,10.1.1.10' (RSA) to the list of known hosts. Enter passphrase for key '/home/mchurchi/.ssh/id_dsa': ∗∗∗∗∗∗ /tmp f1.txt f2.txt d1.dir
NOTE: In the examples above, you didn't have to enter the user password. Rather, you enter the passphrase that you set with the ssh-keygen command.. If you would rather not have to enter a passphrase when accessing the remote host, create an empty passphrase when prompted for the ssh-keygen passphrase. Now, you won't have to type anything to access the remote host.

Be the first to comment.
Leave a response